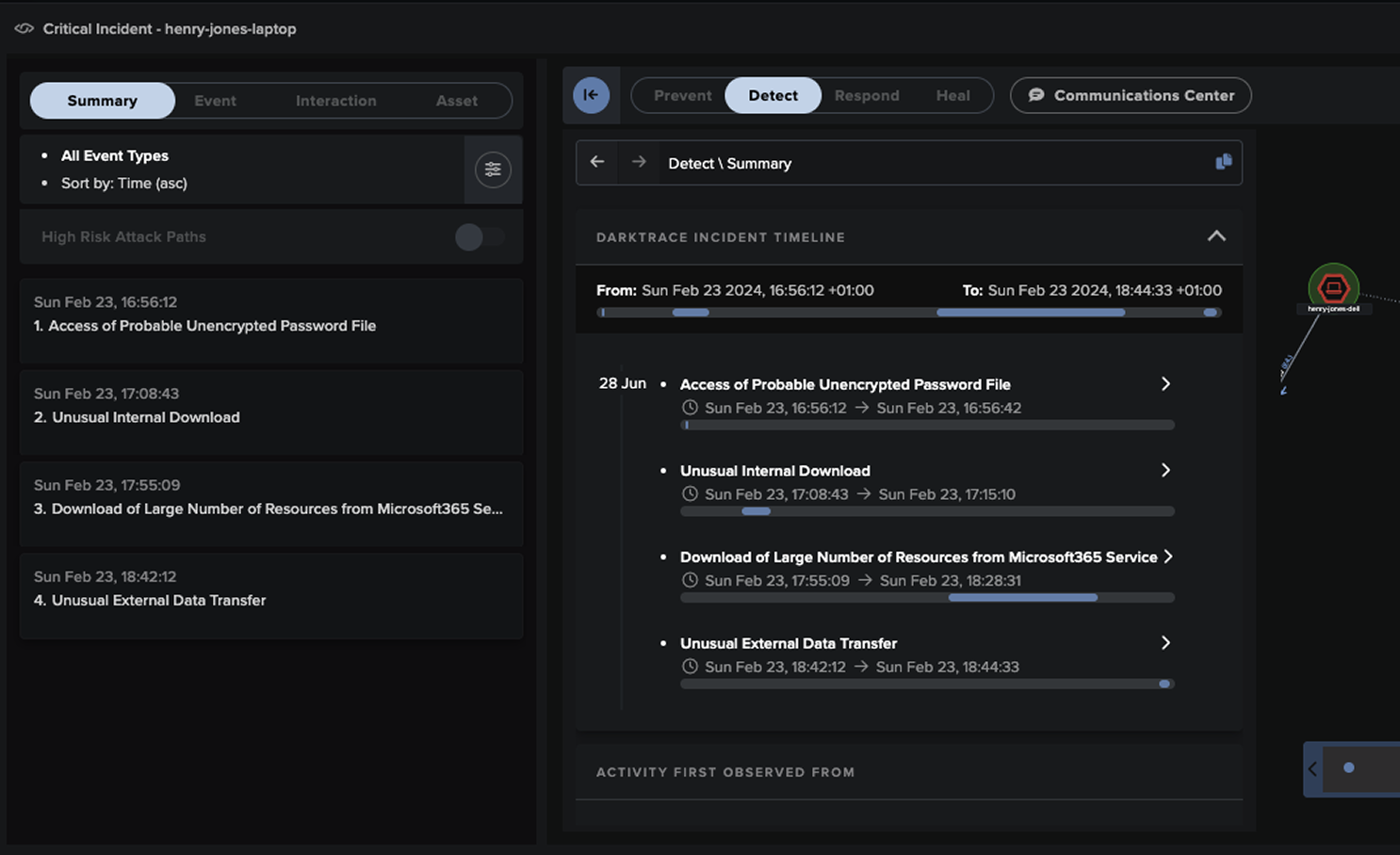
Darktrace® adressiert eine zentrale Herausforderung moderner IT-Sicherheitsarchitekturen: die frühzeitige Erkennung und autonome Abwehr unbekannter, hochgradig dynamischer Bedrohungen, die sich herkömmlichen, signaturbasierten Lösungen entziehen. Anstelle statischer Regeln nutzt Darktrace® selbstlernende KI-Algorithmen, die das normale Verhalten von Nutzern, Geräten und Systemen in Echtzeit modellieren. Auf dieser Basis erkennt das System verhaltensbasierte Anomalien, etwa bei lateralen Bewegungen, untypischer Datenexfiltration oder internen Bedrohungen – unabhängig von vorab bekannten Angriffsmustern.
Das Modul Darktrace® Antigena ermöglicht eine automatisierte, kontextbasierte Reaktion: verdächtige Verbindungen werden isoliert, kompromittierte Identitäten temporär blockiert oder Datenflüsse unterbrochen – präzise und ohne operative Unterbrechung.
Darktrace® etabliert eine adaptive, autonome Sicherheitslage, die klassische Präventionsmechanismen ergänzt und insbesondere in hybriden, cloudbasierten und hochgradig vernetzten IT-Umgebungen effektiven Schutz auf Enterprise-Niveau bietet.